Cloud Atlas Asset Exposure Surface Management Platform
Risk Management in a Complex World
Apply for a TrialLoginDownload Whitepaper
Risk Governance Platform from the Attacker’s Perspective
Continuous Protection from Enterprise Assets
Asset Mapping
Know what you have
Attack Surface Analysis
Attacker's Perspective
Continuous Security Inspection
Know what to fix
Priority Ranking
Prioritize
Risk Alerting & Remediation
Accelerate remediation
Discover and Map Enterprise Assets with Correlation Graphs
Backed by 10+ years of white-hat penetration testing experience, trillions of accumulated fingerprints/dictionaries, continuous third-party data sources, vulnerability databases, and security community scans. Through open APIs and automated penetration testing systems, Cloud Atlas dynamically maps assets across internet-facing environments, including on-premises data centers, cloud resources, subsidiaries, and supply chains. It identifies 66%+ unknown/hidden assets on average, supporting grouping, tagging, and lifecycle management.


0%+
Average discovery rate of 66% unknown/hidden assets for enterprises
0+
Security communities/white-hat intelligence sources
Quadrillion+
Attack intelligence data points archived
0+ Years
Penetration testing experience
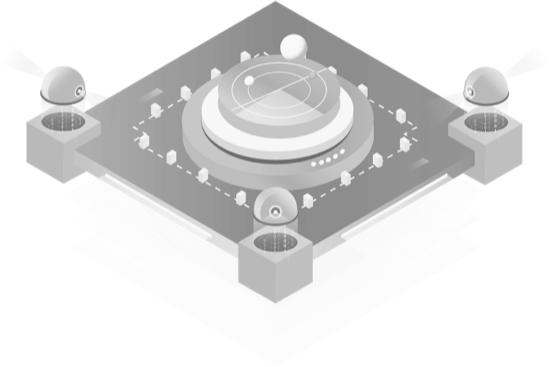
Core Architecture: Effortlessly Tackle Complexity

Core Advantages
Trillion-level Intelligence Repository, Precision Asset Scanning
Backed by a robust asset data center, Cloud Atlas conducts periodic large-scale mapping to accumulate data and intelligence. Leveraging over 10 years of white-hat penetration testing experience, it integrates hundreds of billions of DNS subdomain enumeration dictionaries, zone transfer vulnerability plugins, and third-party data API interfaces. Through refined empirical rules and third-party capability integration, Cloud Atlas excels in asset discovery and management across massive, complex scenarios.
"Attacker’s Perspective" Is More Than a Slogan
Built on Chaitin’s offensive-defense DNA and supported by a powerful security service team, Cloud Atlas covers a broad spectrum of risks. By performing attack path correlation analysis, it helps customers map a complete attack landscape from an attacker’s viewpoint, rapidly identify attack paths, and respond decisively—maximizing product efficiency.
SaaS Model with Zero Deployment, Adaptive Elastic Scaling
The subscription-based model offers flexible deployment and purchasing options. Additionally, Cloud Atlas leverages global multi-node cloud computing resources to deliver adaptive elastic scaling, effortlessly handling high-traffic scenarios while reducing costs and improving efficiency.
