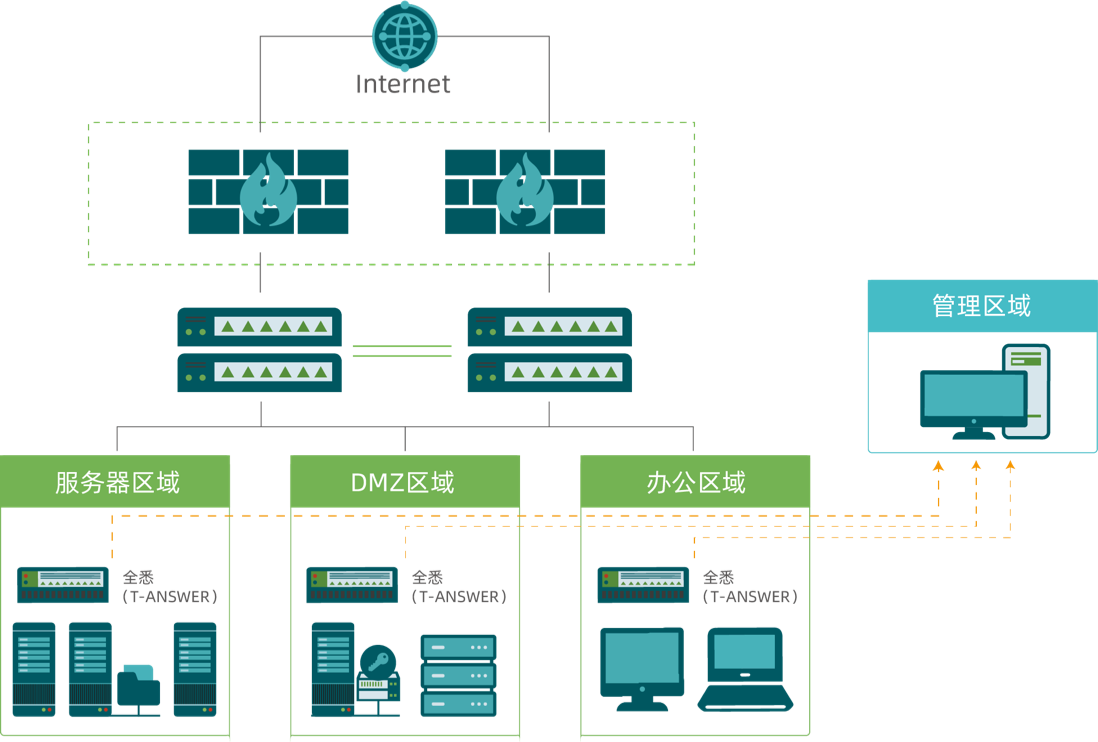
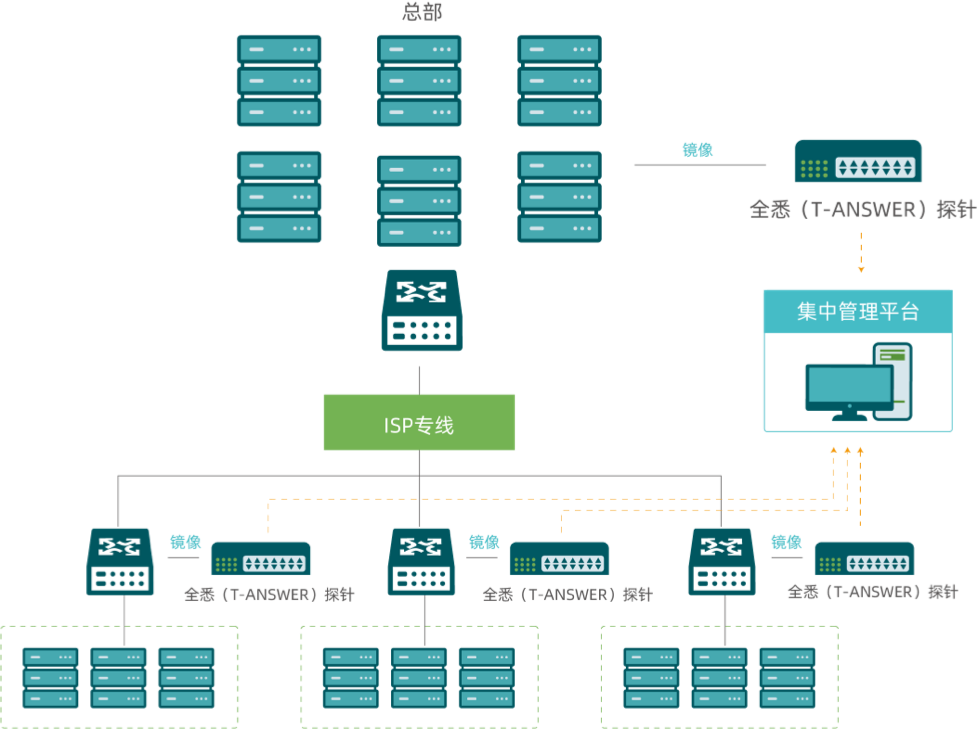
Product Architecture



Detection Capabilities
Bidirectional Full Traffic Inspection
Bidirectional flow analysis technology
Data traffic parsing
Red Team Arsenal Detection
Identification of red team toolkits
Real-world attack and defense perations detection rules
AI-powered behavioral detection model for red team activities
Smart Semantic Analysis 2.0
Upgraded algorithms for detecting 0day exploits, polymorphic attacks, and APTs
Internal network penetration threat detection
Recognition of common lateral movement techniques
AI-Driven Malicious Encrypted Traffic Detection
Detects encrypted reverse shells, ICMP/DNS/HTTP covert tunnels, and encrypted tool-based intrusions
Virtualization Platform Threat Detection
Pinpoints attacks targeting VMware vCenter, ESXi, and other hypervisors
Intelligent Malware File Detection
Dynamic-static hybrid analysis for viruses, Trojans, hacker tools, rootkits, and cryptominers
Cyber-Kill-Chain Coverage
End-to-end detection aligned with attack lifecycle stages
WebShell Detection
Multi-algorithm approach (static + dynamic)
Deep inspection of malicious code patterns
Threat Intelligence Integration
Built-in threat intelligence engine
Real-time updates with global threat feeds
Analysis & Investigation
Multi-Dimensional Traceability Analysis
Covers threat intelligence, threat logs, metadata, threat PCAP packets, and full-traffic data storage.
Intelligent Aggregation & Investigation
Automated aggregation analysis from attacker, victim, and threat event perspectives to improve efficiency and reduce noise.
Knowledge Graph Visualization
Leverages knowledge graph technology to visually map attack chains.
Response & Mitigation
Proactive Blocking
"Mimic Defense" Integration
Third-Party Firewall Collaboration
Security Analysis & Management Platform Integration
Host Security Management Platform "Network-End" Coordination
Product Value
Security Risk Operation
"Intelligence Officer"
Advanced Threat Detection & Response
"Commander"
Smart Traceability Investigation
"Analyst"
Compliance with Multi-level Protection
Scheme (MLPS) 2.0
Application Scenarios
- Daily Security
Operations & Compliance - Advanced Threat
Detection & Response - Centralized Monitoring
for Complex Architectures
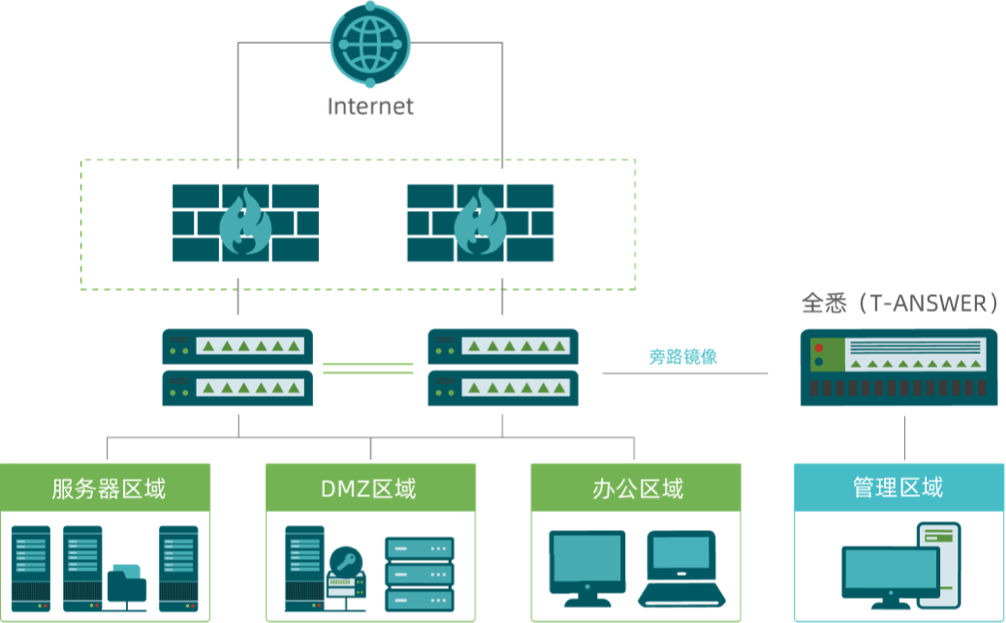
Alleviates compliance evaluation pressures and enables traffic control.
- Deploys inline with existing enterprise networks via passive mirroring for effective threat detection.
- Identifies compromised hosts and remote-controlled assets for security audits.
- Meets Classified Protection 2.0 requirements by detecting unknown threats.